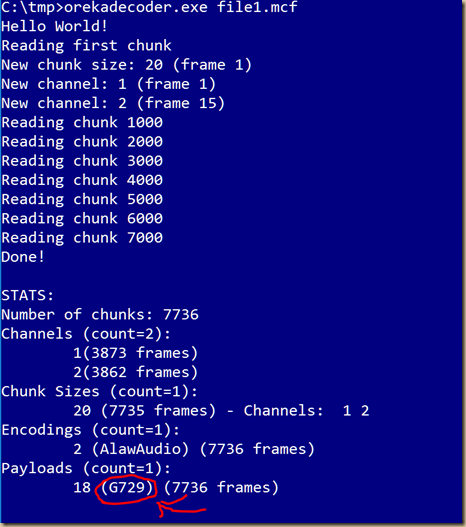
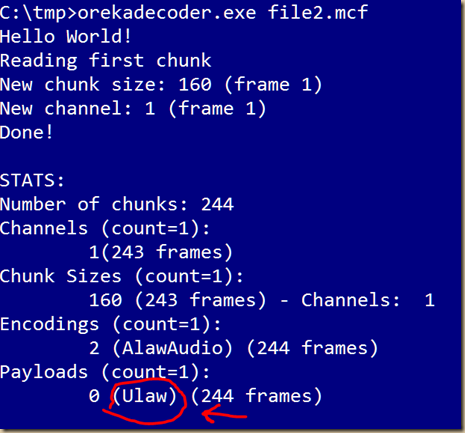
Hi all, been wayy way to long since i last updated and wrote in this blog. Been super busy and i hope you guys too have had a wonderful year as i had and super grateful for it :-)
Here’s a quick article for anyone wishing to integrate Telegram messaging to NagiosXI quick. Telegram is amazing, its free, its fast, its secure. Their API is also an official one (unlike Whatsapp)
CRITICAL NOTICE:Take note, Telegram can sometimes go down, your internet can also go do, for some reason, Nagios server may not have access to internet, so it will not send Telegram messages, always use email or SMS as a backup.
What do you need? And what i assume..
- A NagiosXI installation that can access the internet at all times (as it sends to Telegram servers over the internet)
- Subscribe/register with Telegram (Mobile app Appstore, Play Store or Web - https://web.telegram.org/). A mobile number is required.
- I like to send to a group, so create a group called “NagiosAlerts” in your Telegram or any name that you like, do not use spaces or special characters please. Add at least one more person into that group (e.g. your team that has Telegram installed). This guide assumes sending to that group “NagiosAlerts”, you can change that as per script (the send_telegram.sh script) below.
- This guide was based on Centos 7, i cannot imagine it too much different to Centos6 or RHEL6 / 7, modify the part of yum, that would be the only problematic one, if at all
- You have sufficient XI and linux commands know-how
Let’s begin, you’re a couple of steps away from Telegramming on NagiosXI!
This article assumes you’ve got XI installed already. So we can dive straight into the telegram setup bit. You can send messages many ways, you can use the bot method or use an actual Telegram user. I prefer to use the user way. Do it whichever way you’d like, this guide however is based on user and group.
Run from your Nagios CLI via SSH as root. Cut and paste where applicable. Italic items of course don’t cut and paste lah
- yum install lua-devel openssl-devel libconfig-devel readline-devel libevent-devel jansson-devel.x86_64 python-devel git -y
- cd /usr/src/
- git clone --recursive https://github.com/vysheng/tg.git
- mkdir /usr/local/nagios/telegram
- mv tg /usr/local/nagios/telegram
- cd /usr/local/nagios/telegram/tg
- ./configure
- make
- chown nagios.nagios /usr/local/nagios/telegram/ –R
Now, let’s test run it for the first time to perform registration as user nagios or whichever nagios user you have configured nagios for (usually “nagios”). Take note on the phone number format as explained below
- su nagios
- bin/telegram-cli -k tg-server.pub
- When asked for phone, enter your number e.g. +6012123456 (enter with country code and plus sign at the beginning). Try and use your company phone numbers so its “nothing personal”. You should receive a code via SMS or Telegram, enter the code correctly, then type quit to exit as mentioned below
- quit
- Type exit to go back as root (since you’re now user nagios@)
Now you’re done with telegram, time to setup send message script and let’s use a simple bash script to do that by copying and pasting items in the Courier New font (taken and modified from https://github.com/andy-partington/nagios-telegram/blob/master/telegram_message.sh). Once pasted, save and exit editor.
- vi /usr/local/nagios/libexec/send_telegram.sh .
- chmod +x /usr/local/nagios/libexec/send_telegram.sh && chown nagios:nagios /usr/local/nagios/libexec/send_telegram.sh
#!/bin/bash
NAGMSG="$1"
cd /usr/local/nagios/telegram/tg/
(sleep 3; echo "msg NagiosAlerts '$NAGMSG'"; echo 'safe_quit';) | /usr/local/nagios/telegram/tg/bin/telegram-cli -W -k server.pub -v
Test this now, by going in as user nagios
- su nagios
- /usr/local/nagios/libexec/send_telegram.sh 'Telegram With Nagios Rawks'
- exit
Now, access your XI Web UI, and its time to configure telegram notification via XI. Paste items in bold when requested to, word for word! Only the ones in bold OK!
- In Core Configuration Manager, go to commands, create a new one, call it notify-host-by-telegramcli and the command paste this below
$USER1$/send_telegram.sh "***** Nagios Monitor XI Alert *****\n\nNotification Type: $NOTIFICATIONTYPE$\nHost: $HOSTNAME$\nState: $HOSTSTATE$\nAddress: $HOSTADDRESS$\nInfo: $HOSTOUTPUT$\n\nDate/Time: $LONGDATETIME$\n" - As for the type set it to “Misc Command”
- Click Save
- In Core Configuration Manager again, go to commands, create a new one, call it notify-service-by-telegramcli and the command paste this below
$USER1$/send_telegram.sh "***** Nagios Monitor XI Alert *****\n\nNotification Type: $NOTIFICATIONTYPE$\n\nService: $SERVICEDESC$\nHost: $HOSTALIAS$\nAddress: $HOSTADDRESS$\nState: $SERVICESTATE$\n\nDate/Time: $LONGDATETIME$\n\nAdditional Info:\n\n$SERVICEOUTPUT$" - Again, type is “Misc Command”
- Click Save
- Click Apply Configuration and now you’re ready to add the notification type to relevant users, eg. nagiosadmin
- Modify the contacts to include (or exclusively use) telegram, select host for host, select service for service. Below is example of host and followed by service
This is for host
This is for service
- Save and apply. Go ahead and test by sending custom notification for a host or service where your configured contact will get messages, of course, that contact must be part of the contact that will receive notification for the respective service or host. If you can’t get messages, then its likely notification for that user you enabled isn’t using telegram method or something else isn’t right within Nagios notification logic. Check the relevant logs. See if its even sending to begin with…you should see something like below;
SERVICE NOTIFICATION: nagiosadmin;localhost;Current Users;CUSTOM (OK);notify-service-by-telegramcli;USERS OK - 2 users currently logged in;Nagios Administrator;did i get this on telegram? - Check logs with;
tail -100 /var/log/messages
So you’re done. Easy peasy innit?
MERRY CHRISTMAS and HAPPY NEW YEAR. Many cheers from Astiostech too!