Quoted off http://www.eweek.com/c/a/Data-Storage/Cisco-Buys-PostPath-to-Compete-with-Microsoft-Exchange/
"Cisco Systems acquired PostPath, a Microsoft Exchange e-mail storage competitor, and heads down the path of a big-time "co-opetition" to handle enterprise e-mail against a longtime partner, Microsoft. PostPath uses augmented open-source software and an optional appliance that plugs directly into a data center to offer a lower-cost, in-the-cloud e-mail server alternative to Microsoft Exchange. Exchange has long been known as one of the most complicated business software packages that IT personnel handle."
Nevertheless, if you are looking for a powerful email client/server that brushes shoulders with Exchange, try www.zimbra.com, their web mail is simply magnificent. They have a 100% open source version readily available for download/use.
---Sharing some frustration---
I've been using, consulting on and supporting Exchange for years and up to 2007, its a superb product but you need people with a PhD in Exchange to get it working properly. This is mainly due to complex integration with Active Directory and other Windows components. Exchange 2007 installation takes hours! But once its done, you can go straight down to Powershell and start managing it scriptly...something MS should have thought of and done yeaaaars ago. GUI is great, but lets face it, ..it introduces bulk and possible coding errors etc thus creating a risk to the core functionality of Exchange itself. And what the heck is the deal with the 5 roles, 2 roles i understand, email and voice features, finito, no, here we have 5 roles. Why? To buy more Exchange boxes. Hello Microsoft, hear me, hear me, people are trying to save cost and simplify stuff, why complicate things even more? Oh, wait Sanjay, is scalability, ermm...hey dudes, so you basically kicking Exchange 2003 and its predecessors in their nuts heh? Not scalable issit? Hey, those pre-2007 products are just aye okay....
Sometimes i ask the question, are all the features of Exchange 2007 really necessary? I mean, really, really necessary? Are we at the point of saturated ideas and ideology of innovation? I would love to know how many of us use anything in Exchange except the Email, Contacts and Calendaring as often? You probably answered, hmm..true (if you are not a MS advocate).
I met a friend who works for Microsoft while going for a quick "breather" below the lobby of the Malaysian Twin Towers and i asked her, hey, how's TechED 2008 (i didn't attend..didn't have enough money..:P ) and peculiarly, being in a very strategic and influential front of the company she replied... " What is there to showcase anymore for infrastructure? " I was expecting a chuckle or smile but she starred sharply and confidently at me. And come to think of it, its probably true. I mean, another question i ask you fellow readers, how many features in Active Directory do you actually use/need?
Will Exchange ever be simplified? I hope so...
Asterisk and Nagios enthusiasts, professionals and consultants based in Kuala Lumpur, Malaysia. Astiostech Sdn Bhd. Asterisk Malaysia. Nagios Malaysia.
Thursday, August 28, 2008
Tuesday, August 5, 2008
Asterisk Appliance and Fax

Hi all, just a little update on the faxing effort that was attempted from a FreePBX trunked via a IAX2 tunnel to an Asterisk Appliance failed miserably.
Fact of the matter is faxing through Asterisk Appliance is a no go. Even using an ATA adaptor in between the fax machine and the Asterisk Appliance didn't handshake. Sending and receiving.
Workaround: Since we had a FreePBX running, we registered the ATA to this server instead of the Asterisk Appliance and viola...it works like a charm (although sending faxes seem to be a little tricky..sigh)
Anyway, just an update
Thursday, July 31, 2008
Free Microsoft Exchange Monitor, by Solarwinds
Since a while now, i've been a huge fan of Solarwinds (http://www.solarwinds.com) before knowing and falling in love with Nagios (www.nagios.org). Well, this post isn't to harp on the sexy Nagios but to talk about a quick monitoring tool for Exchange servers. Solarwinds released their monitoring tool for Exchange and i like it for its simplicity to use.
The most significant part is that it's free, which means, go download it even if you don't plan to use it (haha). Here's the link. http://www.solarwinds.com/register/index.aspx?Program=825&c=70150000000Djc6
The good thing about this tool, it not only does monitoring of basic OS health but the health of Exchange at the application level.
Exchange, as many of us know, is like an infant, she will cry bloody murder if you don't stick a suckle up her mouth every once in a while. But, lets admit it, who has the time to stare blankly at the ugly perfmon (Windows Performance Monitor) or run dry WMI scripts to spring VB's blend popups if there's something odd, out of the ordinary odd (i like scripting better tho).
This a true free engine unlike the many baits set out there to lure you into the overly abused word FREE (opensource aside) which won't sneak a time-bomb behind you or skin features down to mere lousy 2 functions of the 1000000 functions a paid one can do. I hope those developers who lure public into these monkeytraps just make their software GPL.
Anyway, why i like this piece is cuz it checks;
The most significant part is that it's free, which means, go download it even if you don't plan to use it (haha). Here's the link. http://www.solarwinds.com/register/index.aspx?Program=825&c=70150000000Djc6
The good thing about this tool, it not only does monitoring of basic OS health but the health of Exchange at the application level.
Exchange, as many of us know, is like an infant, she will cry bloody murder if you don't stick a suckle up her mouth every once in a while. But, lets admit it, who has the time to stare blankly at the ugly perfmon (Windows Performance Monitor) or run dry WMI scripts to spring VB's blend popups if there's something odd, out of the ordinary odd (i like scripting better tho).
This a true free engine unlike the many baits set out there to lure you into the overly abused word FREE (opensource aside) which won't sneak a time-bomb behind you or skin features down to mere lousy 2 functions of the 1000000 functions a paid one can do. I hope those developers who lure public into these monkeytraps just make their software GPL.
Anyway, why i like this piece is cuz it checks;
- In real time
- General Win health checks (like disks , CPU, memory)
- Exchange services
- Mail, PF and SMTP queues (see if they are collectively planning to sink the box down)
- ..and more "sensors", but not a lot of customization
- Pretty little interface to wrap it up but finally
- ITS FREE.
Thursday, July 24, 2008
Free DHCP Server
Hi, been a while since i wrote anything here. Anyway, here's something i just had to share with my friends out there.
If you are in a dire need of a DHCP server (i'm laughing at that statement too..), cause the main one crashed or isn't functioning, then you do not necessarily need to install another Windows box or a Unix server just to start pouring out life into our DHCP client devices. Just fire up your XP (or compatible OS) and start this excellent software called TFTPD32.
Firstly, its FREE, yes, FREE la.
TFTPD is a completely functional DHCP server with a TFTP server and client and a SYSLOG server, all in a tiny under 500k binary. Superb stuff. I had to use it to do a TFTP and DHCP to assign a device while upping a TFTP image off the TFTP server.
Its just too simple to use, for DHCP, just define the scope start and the amount of assignable IPs of that scope and usual stuff like Netmasks and also you can create custom DHCP options. Unfortunately, unlike the infamous DHCP server from Windows, the options are not selectable and if you do not know what options are there, you could Google it or simply click here...http://www.networksorcery.com/enp/protocol/bootp/options.htm .
Finally, this tool is a network arsenal, to
1. Do all of what it's capable of (like DHCP-ing, TFTP-ing...)
2. Turnturtle your ex's network by just plugging in this baby into any network and assign bogus IPs thus causing a DHCP offer from yours and an existing DHCP server ....
Their official website where you could download the software: http://www.jounin.net/tftpd32.html
Screenies from my DHCP setup couple of hours ago

If you are in a dire need of a DHCP server (i'm laughing at that statement too..), cause the main one crashed or isn't functioning, then you do not necessarily need to install another Windows box or a Unix server just to start pouring out life into our DHCP client devices. Just fire up your XP (or compatible OS) and start this excellent software called TFTPD32.
Firstly, its FREE, yes, FREE la.
TFTPD is a completely functional DHCP server with a TFTP server and client and a SYSLOG server, all in a tiny under 500k binary. Superb stuff. I had to use it to do a TFTP and DHCP to assign a device while upping a TFTP image off the TFTP server.
Its just too simple to use, for DHCP, just define the scope start and the amount of assignable IPs of that scope and usual stuff like Netmasks and also you can create custom DHCP options. Unfortunately, unlike the infamous DHCP server from Windows, the options are not selectable and if you do not know what options are there, you could Google it or simply click here...http://www.networksorcery.com/enp/protocol/bootp/options.htm .
Finally, this tool is a network arsenal, to
1. Do all of what it's capable of (like DHCP-ing, TFTP-ing...)
2. Turnturtle your ex's network by just plugging in this baby into any network and assign bogus IPs thus causing a DHCP offer from yours and an existing DHCP server ....
Their official website where you could download the software: http://www.jounin.net/tftpd32.html
Screenies from my DHCP setup couple of hours ago

Friday, April 25, 2008
Monitoring Exchange Unauthorized Mailbox Access (Exchange 360degree monitoring) PART: 1
This is one of the three part security auditing post for Exchange servers.
Many implementers, system integrators, users and administrators implement Exchange servers as part of their collaboration infrastructure without knowing what's going on in Exchange. For security conscious companies/people, its important to know that not only Exchange but any email system put out there have a potential of a security breech, more often than not, they (the threats) may come from inside.
All systems have administrators or superusers which (can) have full control over applications and data inside servers. Now this article focuses on one very important factor when it comes to administering an Exchange server and that is knowing what our administrator does.
Problem with admins being "Gods" on mail server is that they can take ownership of a mailbox on Exchange or associate themselves (or someone other user) to a mailbox thus giving full rights to read other user's emails/data.
Now, that's good for some reasons but it can be seriously become dangerous if for example, this administrator reads his/her bosses email or the CEO's email, for instance.
Facts:
Questions this article plans to address.
In most articles you find online, they address the tracking of events that are associated with anyone accessing mailboxes that are not theirs. That's good, but these articles do not address when someone removes the audit setting. Since admins are Gods, they can do this. Doing this will disable tracking of such events (reversing the auditing).
In all cases where you would like to start monitoring your Exchange based on this 360degree Exchange monitoring document, i suggest audit your existing Exchange for possibly any delegation that are "suspicious". I will not discuss auditing just yet unless its requested.
The steps in general are as below; (i assume you know how to turn auditing events on and off on a Windows box). I suggest use a remote event viewer tracker application like a vbscript (shall show you on a later post) or software like EventSentry to trap events that appear and send emails etc..
Enable global level auditing
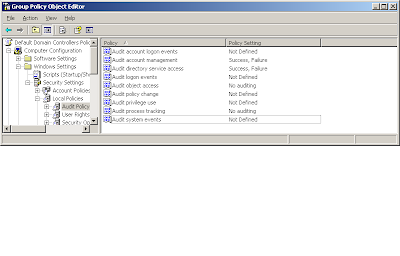 NOTE: You do not have to turn on failure audits and account management audits, i enabled it for other purposes.
NOTE: You do not have to turn on failure audits and account management audits, i enabled it for other purposes.
Enable auditing the changes to global level auditing (360deg)
Now, at this point, if someone edits or removes this policy or the auditing settings, an event will be triggered to give you enough time to capture the event. An event like below can be then captured.
Event Type: Success Audit
Event Source: Security
Event Category: Directory Service Access
Event ID: 566
Date: 4/15/2008
Time: 5:31:37 AM
User: CHAMPS\Administrator
Computer: FIRSTSERVER
Description:
Object Operation:
Object Server: DS
Operation Type: Object Access
Object Type: groupPolicyContainer
Object Name: CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC=champs,DC=int
Handle ID: -
Primary User Name: FIRSTSERVER$
Primary Domain: CHAMPS
Primary Logon ID: (0x0,0x3E7)
Client User Name: Administrator
Client Domain: CHAMPS
Client Logon ID: (0x0,0x1BEB5)
Accesses: Write Property
Properties:
Write Property
Default property set
versionNumber
groupPolicyContainer
Additional Info:
Additional Info2:
Access Mask: 0x20
Notice that the versionNumber is "written" therefore a change to this policy (6AC1786C-016F-11D2-945F-00C04fB984F9 which was the domain controller security policy's GUID) has been made and this event is logged in the Security event on your domain controller. You have to now manually go check if anyone changed this policy to deem it useless for logging :).
Enable diagnostic logging - triggering alerts for non default mailbox access
Now that you've got the auditing at the global level turned on and tracked for changes, we can proceed with the second part. Please note though, diagnostic logging in Exchange is not dependent on the above global logging settings and the events are logged in the Application tab on your Exchange server unlike auditing, where events are stored in the security tab. If this event is triggered, your remote event correlator tool should immediately send an email out. Even if someone tries to clear the event viewer, this event has already been generated so the remove event correlator tool would have picked it up.
Anyway, how to turn on diagnostic logging for the above event..
Now, any non default user access will trigger event 1016 in your application log of that Exchange server. NOTE: If you use clusters, it will be triggered on all the physical servers.
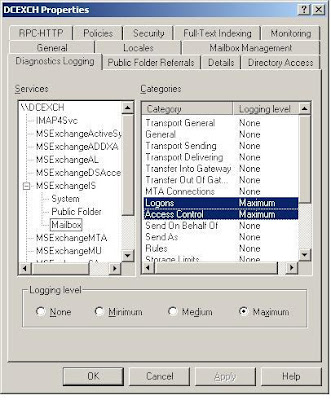
NOTE: You can omit selecting maximum or Access control. I am doing it for some other purposes.
To eliminate false positives, use your monitoring software and filter out the 1016 events for attempts by exchange full administrators. There are instances where other software and system that could trigger this event, these could be;
1. SYSTEM
2. Antivirus account
3. Backup account
4. Blackberry or equivalent software
5. Folders delegation in Outlook (done by users themselves)
Due to the chances of a high false positive rate, it is recommended to only log exchange full administrators like \Administrator alone will do.
Enable auditing the removal of diagnostic logging settings (360deg)
Alright, now that you've got auditing of non default mailbox out of the way, we now attempt to audit anyone removing or changing this setting. This auditing will need the policy setup at the local Exchange server level (unlike above, where you could set it at the domain level). Object Access need to be turned on, on each physical Exchange Servers. Please note that if you have a OU, Domain or Domain Controller or Site group policy that conflicts with this setting, your local settings be overwritten. So, i recommend, group all exchange servers together into one OU, then create a group policy in this OU to enable Object Access Auditing - Success turned on.
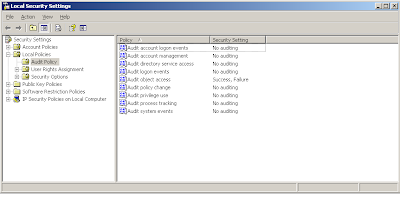 NOTE: You do not need to audit Failure.
NOTE: You do not need to audit Failure.
On each physical Exchange servers, browse to the following registry key
Right click on 9000 Private and click permissions. Click Advanced and click on the auditing tab. Select Everyone or Authenticated Users when prompted for users then track the following like the diagram below;
This registry key basically refers to the diagnostic logging settings. Enabling auditing on this key will track changes made to the key's auditing settings itself and values within this key.
check on the Set Value for success is sufficient. I selected both for other purposes.
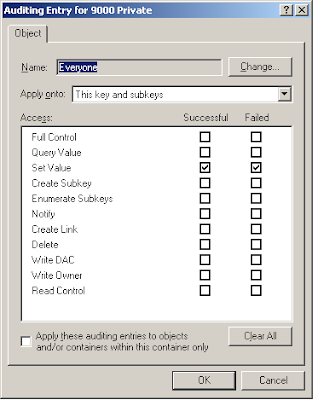
Okay, now that you've set that up, any attempts to modify the diagnostic logging settings and/or the registry settings will be tracked and an event like below shall be triggered.
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Date: 4/17/2008
Time: 1:04:13 AM
User: CHAMPS\Administrator
Computer: SECONDSERVER
Description:
Object Open:
Object Server: Security
Object Type: Key
Object Name: \REGISTRY\MACHINE\SYSTEM\ControlSet\Services\MSExchangeIS\Diagnostics\9000 Private
Handle ID: 1340
Operation ID: {0,2242247}
Process ID: 2148
Image File Name: C:\WINDOWS\system32\mmc.exe
Primary User Name: Administrator
Primary Domain: CHAMPS
Primary Logon ID: (0x0,0x21F7F)
Client User Name: -
Client Domain: -
Client Logon ID: -
Accesses: Query key value
Set key value
Enumerate sub-keys
Privileges: -
Restricted Sid Count: 0
Access Mask: 0xB
Alright, there you go, happy auditing. Be secure, start by knowing and gaining visibility.
Many implementers, system integrators, users and administrators implement Exchange servers as part of their collaboration infrastructure without knowing what's going on in Exchange. For security conscious companies/people, its important to know that not only Exchange but any email system put out there have a potential of a security breech, more often than not, they (the threats) may come from inside.
All systems have administrators or superusers which (can) have full control over applications and data inside servers. Now this article focuses on one very important factor when it comes to administering an Exchange server and that is knowing what our administrator does.
Problem with admins being "Gods" on mail server is that they can take ownership of a mailbox on Exchange or associate themselves (or someone other user) to a mailbox thus giving full rights to read other user's emails/data.
Now, that's good for some reasons but it can be seriously become dangerous if for example, this administrator reads his/her bosses email or the CEO's email, for instance.
Facts:
- By design, one user can only have one mailbox (that's called the primary user for this mailbox)
- By design since Exchange 2000, administrators have been denied access to other users mailbox out of the box
- By design, when admins do this (associate themselves or other users to another mailbox), no one knows (or nothing is logged) on the Windows box hosting Exchange or Active Directory servers
Questions this article plans to address.
- Can we track when someone access a mailbox that does not belong to him/her
- Can we track if the auditing are disabled.
In most articles you find online, they address the tracking of events that are associated with anyone accessing mailboxes that are not theirs. That's good, but these articles do not address when someone removes the audit setting. Since admins are Gods, they can do this. Doing this will disable tracking of such events (reversing the auditing).
In all cases where you would like to start monitoring your Exchange based on this 360degree Exchange monitoring document, i suggest audit your existing Exchange for possibly any delegation that are "suspicious". I will not discuss auditing just yet unless its requested.
The steps in general are as below; (i assume you know how to turn auditing events on and off on a Windows box). I suggest use a remote event viewer tracker application like a vbscript (shall show you on a later post) or software like EventSentry to trap events that appear and send emails etc..
- Enable auditing of directory access at the global level - I suggest turning this on at the domain controller security policy) - This is to audit changes made to the audit settings (explained later)
- Enable audit of changes made to the domain controller security policy
- Enable diagnostic logging setting for Logons, under MSExchangeIS, Mailbox
- Enable auditing the removal of the diagnostic logging
Enable global level auditing
- Launch Active Directory Users and Computers, go to Domain Controllers and edit the Default Domain Controller Security Policy (or use GPMC) or you could use a new one to avoid changing this default policy
- Go to Computer Configuration, Windows Settings, Security Settings, Audit Policy
- Turn on Audit Directory Service Access - Success
 NOTE: You do not have to turn on failure audits and account management audits, i enabled it for other purposes.
NOTE: You do not have to turn on failure audits and account management audits, i enabled it for other purposes.
Enable auditing the changes to global level auditing (360deg)
- Launch Active Directory Users and Computers, go to Domain Controllers and click Properties of Default Domain Controller Security Policy (or use GPMC) or the security policy that you've used in the step above.
- Click on Auditing, click Add...
- When prompted for a user, this is the part where you need to monitor all users making changes to this policy, so select Everyone or Authenticated Users
- Click on Properties at the next dialog box..., select Write All Properties, click OK several times until you go back to the ADUC's GPO objects inside that OU. Before quitting that, take note of the GPO's GUID (Unique Name) for use later when an event is triggered.
Now, at this point, if someone edits or removes this policy or the auditing settings, an event will be triggered to give you enough time to capture the event. An event like below can be then captured.
Event Type: Success Audit
Event Source: Security
Event Category: Directory Service Access
Event ID: 566
Date: 4/15/2008
Time: 5:31:37 AM
User: CHAMPS\Administrator
Computer: FIRSTSERVER
Description:
Object Operation:
Object Server: DS
Operation Type: Object Access
Object Type: groupPolicyContainer
Object Name: CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC=champs,DC=int
Handle ID: -
Primary User Name: FIRSTSERVER$
Primary Domain: CHAMPS
Primary Logon ID: (0x0,0x3E7)
Client User Name: Administrator
Client Domain: CHAMPS
Client Logon ID: (0x0,0x1BEB5)
Accesses: Write Property
Properties:
Write Property
Default property set
versionNumber
groupPolicyContainer
Additional Info:
Additional Info2:
Access Mask: 0x20
Notice that the versionNumber is "written" therefore a change to this policy (6AC1786C-016F-11D2-945F-00C04fB984F9 which was the domain controller security policy's GUID) has been made and this event is logged in the Security event on your domain controller. You have to now manually go check if anyone changed this policy to deem it useless for logging :).
Enable diagnostic logging - triggering alerts for non default mailbox access
Now that you've got the auditing at the global level turned on and tracked for changes, we can proceed with the second part. Please note though, diagnostic logging in Exchange is not dependent on the above global logging settings and the events are logged in the Application tab on your Exchange server unlike auditing, where events are stored in the security tab. If this event is triggered, your remote event correlator tool should immediately send an email out. Even if someone tries to clear the event viewer, this event has already been generated so the remove event correlator tool would have picked it up.
Anyway, how to turn on diagnostic logging for the above event..
- Launch Exchange System Manager
- Drill down to your Exchange server's physical name, right click and click properties
- Go to the diagnostic logging tab, go to MSExchangeIS and select Mailbox
- Select logons and set that to minimum (will do)
Now, any non default user access will trigger event 1016 in your application log of that Exchange server. NOTE: If you use clusters, it will be triggered on all the physical servers.

NOTE: You can omit selecting maximum or Access control. I am doing it for some other purposes.
To eliminate false positives, use your monitoring software and filter out the 1016 events for attempts by exchange full administrators. There are instances where other software and system that could trigger this event, these could be;
1. SYSTEM
2. Antivirus account
3. Backup account
4. Blackberry or equivalent software
5. Folders delegation in Outlook (done by users themselves)
Due to the chances of a high false positive rate, it is recommended to only log exchange full administrators like \Administrator alone will do.
Enable auditing the removal of diagnostic logging settings (360deg)
Alright, now that you've got auditing of non default mailbox out of the way, we now attempt to audit anyone removing or changing this setting. This auditing will need the policy setup at the local Exchange server level (unlike above, where you could set it at the domain level). Object Access need to be turned on, on each physical Exchange Servers. Please note that if you have a OU, Domain or Domain Controller or Site group policy that conflicts with this setting, your local settings be overwritten. So, i recommend, group all exchange servers together into one OU, then create a group policy in this OU to enable Object Access Auditing - Success turned on.
 NOTE: You do not need to audit Failure.
NOTE: You do not need to audit Failure.
On each physical Exchange servers, browse to the following registry key
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MSExchangeIS\Diagnostics\9000 Private
Right click on 9000 Private and click permissions. Click Advanced and click on the auditing tab. Select Everyone or Authenticated Users when prompted for users then track the following like the diagram below;
This registry key basically refers to the diagnostic logging settings. Enabling auditing on this key will track changes made to the key's auditing settings itself and values within this key.
check on the Set Value for success is sufficient. I selected both for other purposes.

Okay, now that you've set that up, any attempts to modify the diagnostic logging settings and/or the registry settings will be tracked and an event like below shall be triggered.
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Date: 4/17/2008
Time: 1:04:13 AM
User: CHAMPS\Administrator
Computer: SECONDSERVER
Description:
Object Open:
Object Server: Security
Object Type: Key
Object Name: \REGISTRY\MACHINE\SYSTEM\ControlSet\Services\MSExchangeIS\Diagnostics\9000 Private
Handle ID: 1340
Operation ID: {0,2242247}
Process ID: 2148
Image File Name: C:\WINDOWS\system32\mmc.exe
Primary User Name: Administrator
Primary Domain: CHAMPS
Primary Logon ID: (0x0,0x21F7F)
Client User Name: -
Client Domain: -
Client Logon ID: -
Accesses: Query key value
Set key value
Enumerate sub-keys
Privileges: -
Restricted Sid Count: 0
Access Mask: 0xB
Alright, there you go, happy auditing. Be secure, start by knowing and gaining visibility.
Subscribe to:
Comments (Atom)