In this guide, we will setup a mirrored pair of a SATA disk straight from the Debian installer process.
Go through all up to the stage of selecting Partition Disks. Select manual and follow the rest of this guide.
1) Create the initial partition by selecting the disks and saying yes to partition them for both disks.
On both disks
2) Select the first FREE SPACE available
3) Create partition like /boot, /swap and / (root) partitions.
In our case, we will setup 2GB for /boot (enable bootflag), 2GB for /swap and the rest is for / (root). Now, we do not need to mirror /swap so our guide will skip that and our RAID will only monitor and mirror /boot and / (root)
When partitioning, under enter Use as, select physical volume for RAID. See screens below;
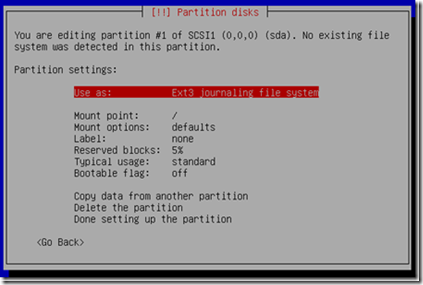
4) Select use as.
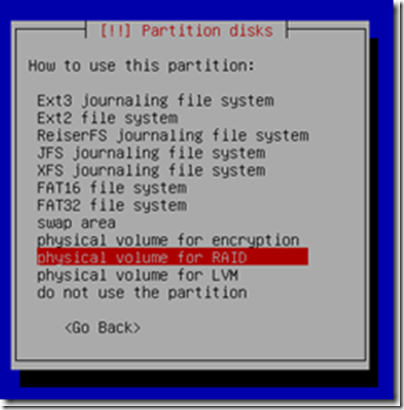
5) Set the boot flag on for /boot for both disks when creating them. For /swap and / (root) you don’t do that. Now, setup /swap and / (root) for both disks as well. Here, since swap is not RAIDed (when selecting -Use as- for the swap partition, select swap area instead) See below for the entire physical architecture.
/boot – use as physical volume for RAID with boot flag on >> becomes sda1 or sdb2
/swap – use as swap >> becomes sda2 or sdb2
/ – use as physical volume for RAID >> becomes sda3 or sdb3
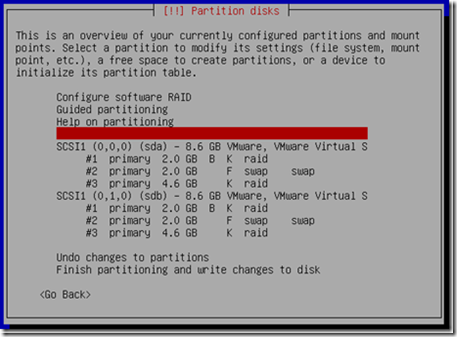
Important: We should have at least a boot, swap and root partition and do this for all other partitions that you want/have.
Enable the RAID virtual volumes
6) Now, select Configure RAID
7) Since we are enabling RAID for 2 partitions, we need to create two Multidisk (MD).
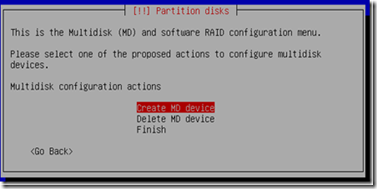
Select Create MD device.
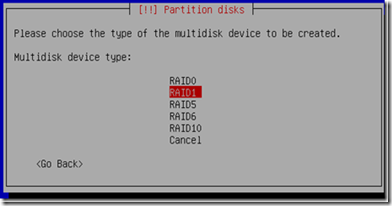
Select RAID1 - Mirror
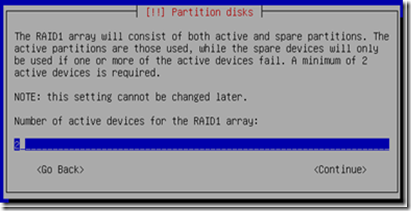
Select accordingly (in mirroring case would naturally be 2), i select 2
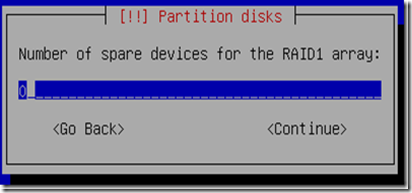
Select spare devices if you have any, i select 0
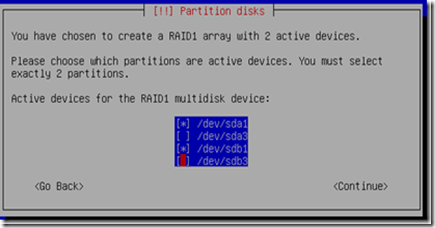
The first MD, md0, we assign it to /boot which are sda1 and sdb1. The second MD, md1, we assign it to /sda3 and sdb3. The above diagram, we are setting up md0, go through creating a new MD, this time, we are left with the rest unassigned partitions.
Configuring the RAID volumes
Once you’ve set it up correctly, you disk layout should look like this;
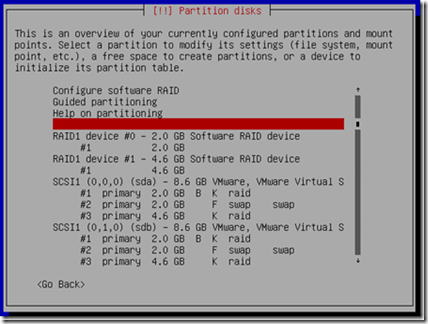
Notice, we have RAID 1 device 0 – which is our /boot and we have RAID 1 device 1 which is our / (root).
8) Now in RAID device 0, select #1 and set that up with Ext3 and select mount point /boot.
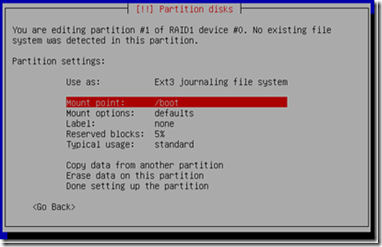
Now, on RAID device 1, select #1 and set that up with Ext3 and select mount point / (root).
9) Eventually, the disk architecture would look like this;
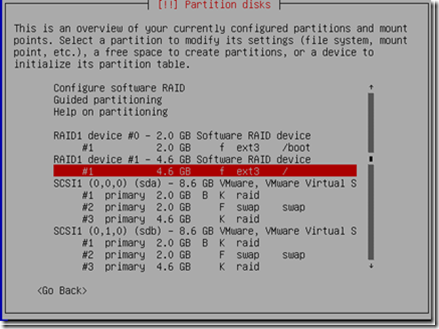
Beside the SCSI 1 and SCSI 2 devices, we now have RAID1 device 0 and device 1 with /boot and / (root) setup.
10) Finally, select Finish….and continue Debian setup till the end, reboot and now you have a RAID 1 configuration.
PS>> The installer might complain about kernel not knowing this and that. Just continue.
After RAID
To check the status of your raid, run
# cat /proc/mdstat
Disk recovery on software RAID
To resync new disks (due to failure whatever), you must do a couple of things. One involves adding the disk to the M0 and M1 volumes and telling grub to install itself in the new disk that you just installed. Here’s how.
Assuming the first disk (sda) failed, and we have replaced and rebooted the server, here’s what all we need to do.
First, we copy the partition structure from sdb (the exiting non failed one) to sda (the new)
# sfdisk -d /dev/sdb | sfdisk --force /dev/sda
Now, we remove any existing raid configs on this new drive (just in case)
# mdadm --zero-superblock /dev/sda1
# mdadm --zero-superblock /dev/sda2
# mdadm --zero-superblock /dev/sda3
[If you get an error, just ignore, meaning you don’t have existing RAID configs in it]
Now, we add back these partition to the RAID MD volumes accordingly
# mdadm -a /dev/md0 /dev/sda1
# mdadm -a /dev/md1 /dev/sda2
# mdadm -a /dev/md2 /dev/sda3
Now, we would like to see the raid resyncing
# cat /proc/mdstat
After that, we must tell grub to enable itself on the newly added disks.
# grub
[The above grub command will end you up in the grub shell, once in this shell, enter the following info]
grub> root (hd0,0)
grub> setup (hd0)
grub> root (hd1,0)
grub> setup (hd1)
grub> quit
This means, i am setting up grub on hd0 and hd1 and so on if you do other types of raid or have more disks etc.
That should get the recovered disks back to speed. Before rebooting, ensure disk sync is completed, keep running
# cat /proc/mdstat
[===========>........]
If the above is happening, it’s still syncing. Don’t reboot yet until these are done.
Good luck.












































